Even madder at Microsoft: The fun never ends with Microsoft. Take the following example. When making a Direct Connection, in the Properties for Incoming Connections, the following is available to view/change:
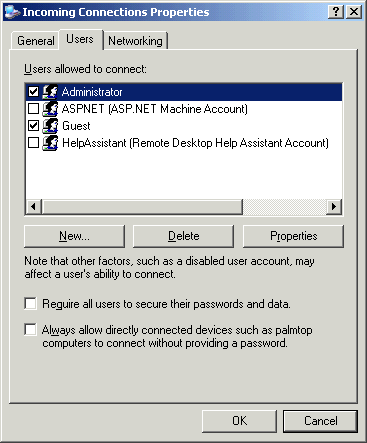
The box at the bottom "Always allow ... connect without providing a password" is unchecked (meaning a password is required).
When a user logs in as Guest, the Network Connections display is:
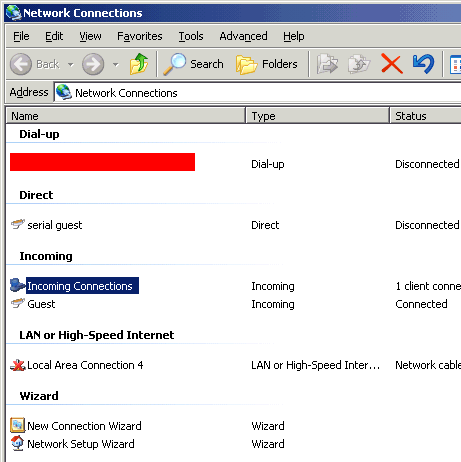
(red box obscures a dial-up identification)
We see Guest as Incoming. Fair enough. But what if we check the box, allowing a connection without a password? Let's log in again, as Guest. Here is the display:
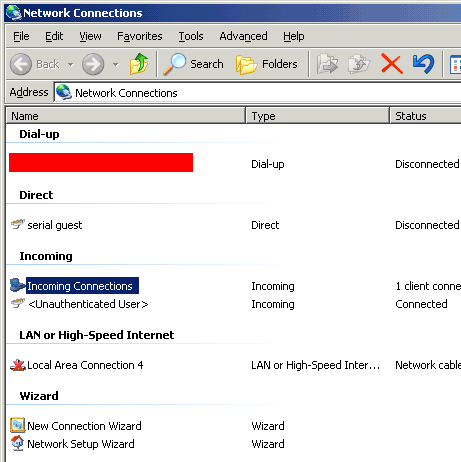
Where is Guest in the listing? All we changed was the password requirement. So, it would stand to reason that a person could connect as Guest, not have to have the password,
and still be seen as Guest. But that's not what's happening. By eliminating the password check, our user is now listed as Unauthenticated User.
And there is no way to find out from the Network Connections display who that user is.
What the hell is going on here?
Who wants to defend this product? (comment freely if you'd like)
Yeah, we know we're focusing on some minor issues, but when you can't get something to work (our current status), you look around trying to make sense of the situation, and the display of misleading or incomplete information makes finding a solution that much harder.
posted by Quiddity at 5/31/2005 04:24:00 AM
Unauthenticated user is more correct and provides more information about the user of the connection than regarding them as "Guest."
Since no password is required, no authentication is performed. The person could enter "Administrator " as their username with no password, and you wouldn't want that showing up in the list, because it would be indistinguishable from a properly authenticated "Administrator" user.
The correct identification is therefore "unauthenticated user."
It may well be that you're giving unauthenticated users the same privelege as an authenticated guest user, but that's essentially beside the point. You could give them any class of priveleges you want.
If you really want more information, you should go into the task manager and see what users own what processes. That provides you a lot more information about what users are doing, and which accounts are active.